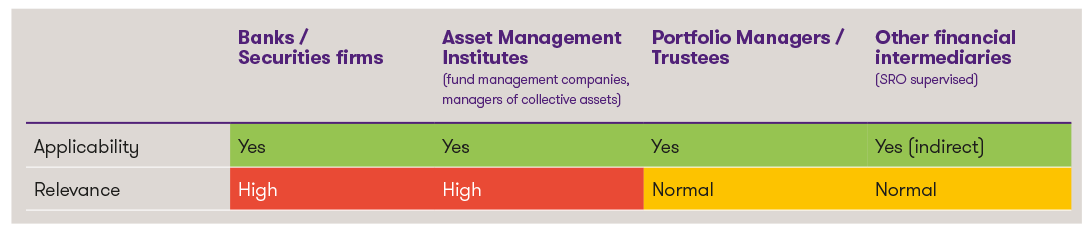
Classification of the innovations1
1 This is a highly simplified presentation intended to enable a quick initial categorisation of the topic. Each institution should determine the relevance and the specific need for action individually and specifically.
Findings from FINMA's cyber risk supervision
Outsourcing
The number of successful attacks on external service providers of supervised institutions is increasing. The reasons for this include the unclear requirements placed on service providers about cyber security and the fact that hardly any checks are carried out. There is a possible need for action as follows:
- Ensure that the requirements are set out clearly enough when concluding contracts with external service providers regarding cyber security
- Regular review of cyber security requirements and its presentation in the control reports
- Clarification of how serious security gaps are recognised by the service providers and quickly closed before damage occurs
- Clarification of whether and how service providers in cyber security are prepared for cyber attacks and what measures can be taken in the event of an attack and within what timeframe (compliance with reporting obligations must be ensured); Definition of processes for reporting obligations
- Ensuring that the cyber security requirements are also met by third parties engaged by the service providers
When outsourcing to service providers, the supervised parties themselves always remain responsible for compliance with regulatory requirements.
Governance and identification
According to FINMA, Cyber risks have not yet been given the necessary priority by the management boards and boards of directors of FINMA-supervised institutions. They are often wrongly treated as a purely technological problem. In addition, there is often a lack of systematic and comprehensive cyber risk management. There is a possible need for action as follows:
- Recognition of cyber risks as an independent risk
- Definition of risk appetite and risk tolerance around cyber risks
- Introduction of key controls in the internal control system (ICS)
- Regular review of the effectiveness of the controls
Protective measures
According to FINMA, there is room for improvement in terms of regular training and testing on cyber risks for employees at all levels. In addition, although many institutions have guidelines and processes for data backup and recovery plans, some of these processes are not tested in the event of a serious cyber attack. In addition, data loss prevention (DLP) measures often only relate to individual databases. There is a possible need for action as follows:
- Conducting regular training for all employees about cyber risks (incl. tests) so that the most common attack methods are recognised and the correct handling of them is trained
- Check whether appropriate data loss prevention (DLP) measures are in place
- Carry out regular tests of the backups created to ensure that they can be restored quickly with the desired up-to-dateness, integrity and completeness (especially in the case of complete encryption incl. data backups due to ransomware attacks)
Detection, response and restoration
Some institutions have, according to FINMA, no or incomplete response plans for cyber incidents or these have not been reviewed for their effectiveness. Specific recovery measures following cyber attacks were also often lacking. Risk-orientated and scenario-based preparation for cyber incidents and crises is therefore crucial and a key success factor for effectively overcoming such stressful situations. There is a possible need for action as follows:
- Development of response plans for cyber incidents (processes and responsibilities)
- Development of recovery measures after cyber attacks
Reporting obligations
FINMA has clarified its Guidance 05/2020 and stated that a report must be submitted to FINMA's key account manager within the first 24 hours of the cyber attack being discovered (informally by email, telephone or similar; including an initial assessment of the criticality and description of the attack). Such a report can be withdrawn at any time if the materiality threshold is not reached. The complete notification must still be submitted via appliaction plattform (EHP) within 72 hours.
The official bank working days apply to the reporting deadlines of 24 or 72 hours. An exception is cyber attacks with a "serious" severity level, which must also be reported to FINMA within 24 hours outside of bank working days. Organisational measures must be taken to ensure that these deadlines can be met.
In the case of outsourcing, it should be noted that the supervised institutions bear the same responsibility as if they were providing the outsourced function themselves. The reporting deadlines therefore begin to run as soon as the institution itself or the third-party provider discovers the cyber incident. The third-party provider must therefore be informed of the reporting obligations and be able to comply with them in cooperation with the institution.
Conclusion
FINMA’s Guidance 03/2024 provides specific information on dealing with cyber risks that is relevant for all institutions supervised by FINMA. Even smaller institutions such as portfolio managers must regularly address cyber risks in the Executive Board and Board of Directors, embed them in risk management and implement controls as part of the ICS. In addition, organisational measures such as appropriate backup strategies and reviews of outsourcing partners about their cyber security and reporting obligations must be reviewed periodically.